- This topic has 1 reply, 1 voice, and was last updated 1 year, 7 months ago by .
Fast-online-transactionsd.shop & world-online.club [Scam Alert]
It has come to our attention that a fraudulent platform operating under the URL fast-online-transactionsd.shop has scammed several individuals by posing as a legitimate shopping site. Victims are lured into placing orders and earning commissions, only to find their funds transferred and irretrievable. One victim, in particular, reported a total loss of $5934 USD, which included multiple transactions amounting to 2950 USDT, 1590 USDT, and 678 USDT sent to the receiving address
 TCKPE86QRz48zTb8f5AvbWLyAi3cPN2nT4
TCKPE86QRz48zTb8f5AvbWLyAi3cPN2nT4 
.
If you have been affected by this scam, please share your story.
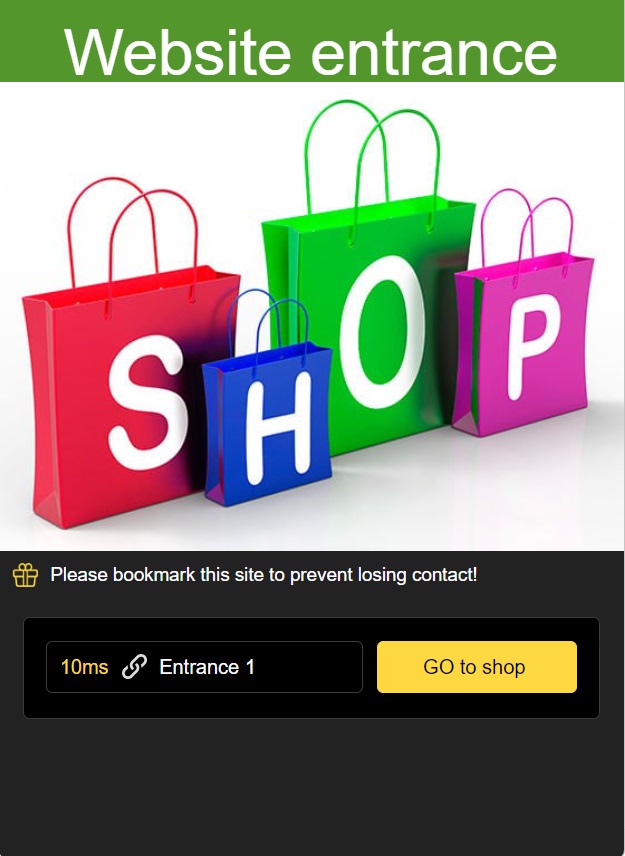
Domain Analysis: fast-online-transactionsd.shop
Fast-online-transactionsd.shop was registered recently, on February 21, 2024, through the registrar GNAME.COM PTE. LTD., and is set to expire on February 21, 2025. The short registration period and the registrar can be initial indicators of fraudulent activities, as scammers often use short-lived domains to avoid detection.
The registrant information indicates that the domain is registered to an entity in Thailand, specifically in the state of ‘man gu’. The registrant’s email, administrative, and technical contact details are obscured, another common tactic used by fraudulent entities to avoid identification and accountability.
The domain is hosted by Cloudflare, Inc., with an IP address associated with Toronto, Canada. Cloudflare is known for providing security and performance solutions, including services that can mask a website’s true hosting details. While Cloudflare is a reputable company, such services can complicate efforts to trace the actual server location and ownership, which scammers often exploit to hide their tracks.
A Semrush analysis indicates that the domain has an authority score of zero and lacks organic search traffic. No significant keywords are associated with the domain; it has only four backlinks from three referring domains. The backlinks are primarily nofollow, which do not pass on SEO value and are often used in low-quality or spammy contexts. The referring domains include ‘xploredomains.com’ and ‘uplinke-seo-optimization.za.com’, which do not appear to be reputable sources, further hinting at dubious activities.
Scam Review: Analysis of fast-online-transactionsd.shop
Upon accessing the website fast-online-transactionsd.shop, a suspicious pattern emerged that aligned with the known characteristics of fraudulent sites. The landing page, labeled “Website entrance,” is simplistic and primarily serves as a gateway with a prominent “GO to shop” button. This initial page urges visitors to bookmark the site to prevent losing contact, a tactic often used to retain potential victims.
Clicking the “GO to shop” button redirects users to another domain, world-online.club (https://www.world-online.club/#/pages/login/login), further raising suspicions. This redirection indicates a scheme to funnel traffic through multiple obscure and potentially fraudulent sites to evade detection and prolong the scam’s operation.
The website design mimics elements of legitimate e-commerce platforms like Shopify, displaying a convincing facade to lure users into entering personal and financial information. The login and registration page on the redirected domain features a professional storefront image. Yet, the request for personal details such as phone numbers and passwords, without secure connections or privacy assurances, is alarming.
The website’s content includes misleading statements and visually appealing images to create a false sense of legitimacy. The primary contact details and regulatory information are conspicuously absent, which is a significant red flag. The site uses phrases like “trusted by millions of businesses worldwide” and high-quality images of luxurious store settings to deceive users into believing they are interacting with a reputable platform.
Upon further inspection of the site’s code and meta tags, it’s evident that the keywords and descriptions are generic, focusing on e-commerce and Shopify without any specific details about the scam site’s actual business operations. This lack of specificity is common among scam websites, allowing them to operate under various facades without committing to a particular identity.
Red Flags
- Domain Redirection: The primary domain fast-online-transactionsd.shop redirects to another domain world-online.club. This tactic frequently confuses users and distributes the scam across multiple platforms.
- Lack of Contact Information: No legitimate contact details, such as addresses, emails, or phone numbers, are provided. The absence of this information makes it difficult to trace or verify the entity behind the website.
- Impersonation of Reputable Platforms: The website impersonates Shopify, a well-known e-commerce platform, to gain users’ trust. This impersonation includes misuse of the Shopify logo and branding elements.
- Urgency Tactics: The site urges users to bookmark the page to avoid losing contact, creating a false sense of urgency and dependency.
- Suspicious Meta Information: The meta tags and descriptions are generic and do not provide any concrete information about the business. They are designed to attract search engines rather than provide transparency to users.
The receiving address
 TCKPE86QRz48zTb8f5AvbWLyAi3cPN2nT4
TCKPE86QRz48zTb8f5AvbWLyAi3cPN2nT4 
has been linked to the scam detailed in the complaint, where the victim was tricked into transferring a total of $5934 to a fraudulent platform. Analysis of the address reveals a pattern consistent with scam operations, as it has been involved in 36 transactions primarily involving Tether USD (USDT). The address shows a current zero balance, indicating that any funds received are quickly transferred out, a common tactic scammers use to evade detection and recovery efforts. The transactions reflect significant amounts being moved frequently, matching the details provided by the complainant about the scam’s modus operandi. This corroborates the complaint and provides substantial evidence linking the address to the fraudulent activities.
Fast-online-transactionsd.shop Reviews
The Google search results reveal significant negative feedback and warnings about the site’s fraudulent activities. Multiple sources, including SafeWebTips and Trustpilot, provide insights into this platform’s dubious nature.
SafeWebTips conducted an in-depth investigation into fast-online-transactionsd.shop, categorizing it under business and financial scams. The investigation highlights several critical issues, such as regulatory troubles and deceptive behavior, aiming to alert users about the potential risks associated with this site. James T., an author on SafeWebTips, stated, “The section labeled as ‘Unreliable’ on Fast-online-transactionsd.shop showcases business and financial services with a track record of underperformance, regulatory troubles, or deceptive behavior.” This underscores the platform’s engagement in schemes that do not meet industry standards and pose significant financial hazards to users.
The site has also been flagged for its low-security score. SafeWebTips reports, “The website’s low-security scores suggest that it might not be effective in safeguarding user data.” This is a crucial red flag, indicating potential vulnerabilities that could lead to data leaks or security breaches, further endangering users’ personal and financial information.
Domain Analysis: world-online.club
The domain world-online.club presents several elements that indicate it might be a part of a broader fraudulent network closely associated with the scam platform fast-online-transactionsd.shop. This domain was registered on July 15, 2024, with Gname.com Pte. Ltd., a registrar associated with other questionable domains. The registration details reveal that the domain is set to expire on July 15, 2025, giving it a short lifespan typical of scam sites designed to operate only for a limited period.
The Whois data for world-online.club shows that it is protected by a clientTransferProhibited and serverTransferProhibited status, limiting any domain transfers during its registration period. The registrant’s details are heavily redacted for privacy, including the registrant’s name, organization, and contact details, all marked as “REDACTED FOR PRIVACY.” The only available geographic information points to “man gu,” Thailand, which mirrors the information from the fast-online-transactionsd.shop domain, suggesting a potential connection between the two.
The redaction of all personal and contact information is a significant red flag, as legitimate businesses typically provide transparent contact details to establish customer trust.
Hosting Checker identifies that the website world-online.club is hosted by CTG Server Ltd., located in Sheung Wan, Hong Kong, with an IP address of 143.92.50.110. Using a hosting provider in Hong Kong, combined with the registrar’s history and the lack of transparency in domain registration, further raises suspicion. The IP address and hosting provider details are crucial for understanding the site’s infrastructure, and the choice of an overseas hosting provider can often be another tactic used by fraudulent entities to evade detection and enforcement actions.
Review Conclusion
Upon thoroughly examining both fast-online-transactionsd.shop and world-online.club, it is evident that these platforms are intricately connected and collectively exhibit numerous hallmarks of a sophisticated scam operation. Both domains were recently registered, have short lifespans, and are associated with dubious registrars known for hosting fraudulent websites. This strategic setup allows scammers to operate under a veil of legitimacy while minimizing the risk of being traced or shut down quickly.
The primary domain, fast-online-transactionsd.shop, serves as the initial point of contact, presenting a facade of an online shopping platform. This site’s use of redirection to world-online.club further complicates the picture, creating a multi-layered scheme designed to confuse users and evade detection by authorities. The redirection tactic is a common method scammers use to spread their activities across multiple domains, making it harder for victims and investigators to piece together the full extent of the fraud.
The Whois data for both domains reveals a pattern of obfuscation, with heavily redacted registrant details and using privacy shields to hide the true identity of those behind the scam. Both domains are linked to the same geographic region in Thailand, suggesting a centralized operation with multiple fronts to enhance their reach and longevity. Hosting these domains on different servers in geographically diverse locations, such as Canada and Hong Kong, adds another layer of complexity designed to frustrate tracking efforts.
In conclusion, the interconnected nature of fast-online-transactionsd.shop and world-online.club and their shared characteristics of recent registration, privacy-shielded ownership, and deceptive content strongly indicate a well-planned scam operation. Users are strongly advised to avoid interactions with these platforms and report any fraudulent activities encountered to the appropriate authorities. The vigilance and collective reporting by the community can help dismantle such fraudulent networks and protect potential victims from financial and personal harm.
- You must be logged in to reply to this topic.